One of many key properties that’s normally hunted for in a cryptoeconomic algorithm, whether or not a blockchain consensus algorithm such a proof of labor or proof of stake, a fame system or a buying and selling course of for one thing like knowledge transmission or file storage, is the best of incentive-compatibility – the concept that it needs to be in everybody’s financial curiosity to truthfully comply with the protocol. The important thing underlying assumption on this purpose is the concept that folks (or extra exactly on this case nodes) are “rational” – that’s to say, that individuals have a comparatively easy outlined set of targets and comply with the optimum technique to maximise their achievement of these targets. In game-theoretic protocol design, that is normally simplified to saying that individuals like cash, since cash is the one factor that can be utilized to assist additional one’s success in nearly any goal. In actuality, nevertheless, this isn’t exactly the case.
People, and even the de-facto human-machine hybrids which are the contributors of protocols like Bitcoin and Ethereum, should not completely rational, and there are particular deviations from rationality which are so prevalent amongst customers that they can’t be merely categorized as “noise”. Within the social sciences, economics has responded to this concern with the subfield of behavioral economics, which mixes experimental research with a set of recent theoretical ideas together with prospect theory, bounded rationality, defaults and heuristics, and has succeeded in making a mannequin which in some instances significantly extra precisely fashions human conduct.
Within the context of cryptographic protocols, rationality-based analyses are arguably equally suboptimal, and there are explicit parallels between a few of the ideas; for instance, as we’ll later see, “software program” and “heuristic” are primarily synonyms. One other focal point is the truth that we arguably don’t even have an correct mannequin of what constitutes an “agent”, an perception that has explicit significance to protocols that attempt to be “trust-free” or have “no single level of failure”.
Conventional fashions
In conventional fault-tolerance idea, there are three sorts of fashions which are used for figuring out how effectively a decentralized system can survive elements of it deviating from the protocol, whether or not attributable to malice or easy failure. The primary of those is easy fault tolerance. In a easy fault tolerant system, the thought is that every one elements of the system will be trusted to do both of two issues: precisely comply with the protocol, or fail. The system needs to be designed to detect failures and recuperate and route round them in some vogue. Easy fault tolerance is normally the perfect mannequin for evaluating techniques which are politically centralized, however architecturally decentralized; for instance, Amazon or Google’s cloud internet hosting. The system ought to undoubtedly be capable to deal with one server going offline, however the designers don’t want to consider one of many servers turning into evil (if that does occur, then an outage is suitable till the Amazon or Google workforce manually determine what’s going on and shut that server down).
Nonetheless, easy fault tolerance isn’t helpful for describing techniques that aren’t simply architecturally, but in addition politically, decentralized. What if we’ve got a system the place we need to be fault-tolerant in opposition to some elements of the system misacting, however the elements of the system is likely to be managed by completely different organizations or people, and you don’t belief all of them to not be malicious (though you do belief that at the very least, say, two thirds of them will act truthfully)? On this case, the mannequin we would like is Byzantine fault tolerance (named after the Byzantine Generals Problem) – most nodes will truthfully comply with the protocol, however some will deviate, and so they can deviate in any approach; the idea is that every one deviating nodes are colluding to screw you over. A Byzantine-fault-tolerant protocol ought to survive in opposition to a restricted variety of such deviations.
For an instance of easy and Byzantine fault-tolerance in motion, a superb use case is decentralized file storage.
Past these two eventualities, there may be additionally one other much more subtle mannequin: the Byzantine/Altruistic/Rational model. The BAR mannequin improves upon the Byzantine mannequin by including a easy realization: in actual life, there is no such thing as a sharp distinction between “sincere” and “dishonest” folks; everyone seems to be motivated by incentives, and if the incentives are excessive sufficient then even nearly all of contributors might effectively act dishonestly – significantly if the protocol in query weights folks’s affect by financial energy, as just about all protocols do within the blockchain area. Thus, the BAR mannequin assumes three sorts of actors:
- Altruistic – altruistic actors at all times comply with the protocol
- Rational – rational actors comply with the protocol if it fits them, and don’t comply with the protocol if it doesn’t
- Byzantine – Byzantine actors are all conspiring to screw you over
In follow, protocol builders are usually uncomfortable assuming any particular nonzero amount of altruism, so the mannequin that many protocols are judged by is the even harsher “BR” mannequin; protocols that survive underneath BR are mentioned to be incentive-compatible (something that survives underneath BR survives underneath BAR, since an altruist is assured to be at the very least nearly as good for the well being of the protocol as anybody else as benefitting the protocol is their specific goal).
Be aware that these are worst-case eventualities that the system should survive, not correct descriptions of actuality always
To see how this mannequin works, allow us to study an argument for why Bitcoin is incentive-compatible. The a part of Bitcoin that we care most about is the mining protocol, with miners being the customers. The “right” technique outlined within the protocol is to at all times mine on the block with the very best “rating”, the place rating is roughly outlined as follows:
- If a block is the genesis block, rating(B) = 0
- If a block is invalid, rating(B) = -infinity
- In any other case, rating(B) = rating(B.mother or father) + 1
In follow, the contribution that every block makes to the overall rating varies with problem, however we are able to ignore such subtleties in our easy evaluation. If a block is efficiently mined, then the miner receives a reward of fifty BTC. On this case, we are able to see that there are precisely three Byzantine methods:
- Not mining in any respect
- Mining on a block apart from the block with highest rating
- Making an attempt to provide an invalid block
The argument in opposition to (1) is easy: in the event you do not mine, you aren’t getting the reward. Now, let us take a look at (2) and (3). Should you comply with the right technique, you have got a chance p of manufacturing a legitimate block with rating s + 1 for some s. Should you comply with a Byzantine technique, you have got a chance p of manufacturing a legitimate block with rating q + 1 with q < s (and in the event you attempt to produce an invalid block, you have got a chance of manufacturing some block with rating damaging infinity). Thus, your block isn’t going to be the block with the very best rating, so different miners should not going to mine on it, so your mining reward won’t be a part of the eventual longest chain. Be aware that this argument doesn’t rely upon altruism; it solely relies on the concept that you have got an incentive to maintain in line if everybody else does – a basic Schelling point argument.
One of the best technique to maximise the prospect that your block will get included within the eventual profitable blockchain is to mine on the block that has the very best rating.
Belief-Free Techniques
One other essential class of cryptoeconomic protocols is the set of so-called “trust-free” centralized protocols. Of those, there are a couple of main classes:
Provably truthful playing
One of many massive issues in on-line lotteries and playing websites is the potential of operator fraud, the place the operator of the positioning would barely and imperceptibly “load the cube” of their favor. A serious advantage of cryptocurrency is its capability to take away this downside by developing a playing protocol that’s auditable, so any such deviation will be in a short time detected. A tough define of a provably truthful playing protocol is as follows:
- In the beginning of every day, the positioning generates a seed s and publishes H(s) the place H is a few normal hash operate (eg. SHA3)
- When a person sends a transaction to make a guess, the “cube roll” is calculated utilizing H(s + TX) mod n the place TX is the transaction used to pay for the guess and n is the variety of attainable outcomes (eg. if it is a 6-sided die, n = 6, for a lottery with a 1 in 927 probability of profitable, n = 927 and profitable video games are video games the place H(s + TX) mod 927 = 0).
- On the finish of the day, the positioning publishes s.
Customers can then confirm that (1) the hash offered firstly of the day really is H(s), and (2) that the outcomes of the bets really match the formulation. Thus, a playing web site following this protocol has no approach of dishonest with out getting caught inside 24 hours; as quickly because it generates s and must publish a worth H(s) it’s mainly sure to comply with the exact protocol appropriately.
Proof of Solvency
One other utility of cryptography is the idea of making auditable monetary companies (technically, playing is a monetary service, however right here we’re taken with companies that maintain your cash, not simply briefly manipulate it). There are strong theoretical arguments and empirical evidence that monetary companies of that kind are more likely to attempt to cheat their customers; maybe probably the most parcticularly jarring instance is the case of MtGox, a Bitcoin trade which shut down with over 600,000 BTC of buyer funds lacking.
The thought behind proof of solvency is as follows. Suppose there may be an trade with customers U[1] … U[n] the place person U[i] has stability b[i]. The sum of all balances is B. The trade desires to show that it really has the bitcoins to cowl everybody’s balances. This can be a two-part downside: the trade should concurrently show that for some B it’s true that (1) the sum of customers’ balances is B, and (ii) the trade is in possession of at the very least B BTC. The second is simple to show; simply signal a message with the non-public key that holds the bitcoins on the time. The only strategy to show the primary is to only publish everybody’s balances, and let folks verify that their balances match the general public values, however this compromises privateness; therefore, a greater technique is required.
The answer includes, as usual, a Merkle tree – besides on this case it is a funky enhanced kind of Merkle tree known as a “Merkle sum tree”. As a substitute of every node merely being the hash of its kids, each node accommodates the hash of its kids and the sum of the values of its kids:
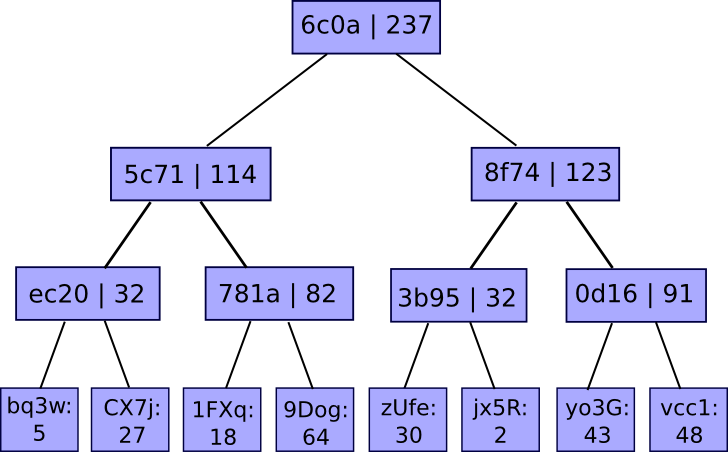
The values on the backside are mappings of account IDs to balances. The service publishes the foundation of the tree, and if a person desires a proof that their account is appropriately included within the tree, the service can merely give them the department of the tree akin to their account:
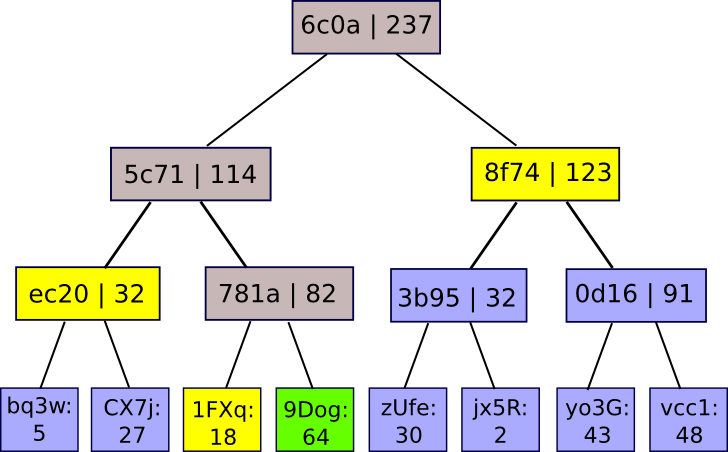
There are two ways in which the positioning can cheat, and attempt to get away with having a fractional reserve. First, it will probably attempt to have one of many nodes within the Merkle tree incorrectly sum the values of its kids. On this case, as quickly as a person requests a department containing that node they are going to know that one thing is fallacious. Second, it will probably attempt to insert damaging values into the leaves of the tree. Nonetheless, if it does this, then except the positioning offers faux optimistic and damaging nodes that cancel one another out (thus defeating the entire level), then there shall be at the very least one official person whose Merkle department will include the damaging worth; on the whole, getting away with having X p.c lower than the required reserve requires relying on a selected X p.c of customers by no means performing the audit process – a consequence that’s really the perfect that any protocol can do, on condition that an trade can at all times merely zero out some proportion of its customers’ account balances if it is aware of that they are going to by no means uncover the fraud.
Multisig
A 3rd utility, and an important one, is multisig, or extra usually the idea of multi-key authorization. As a substitute of your account being managed by one non-public key which can get hacked, there are three keys, of which two are wanted to entry the account (or another configuration, maybe involving withdrawal limits or time-locked withdrawals; Bitcoin doesn’t help such options however extra superior techniques do). The way in which multisig is normally carried out to this point is as a 2-of-3: you have got one key, the server has one key, and you’ve got a 3rd backup key in a secure place. In the midst of regular exercise, once you signal a transaction you usually signal it along with your key domestically, then ship it to the server. The server performs some second verification course of – maybe consisting of sending a affirmation code to your cellphone, and if it confirms that you simply meant to ship the transaction then it indicators it as effectively.
The thought is that such a system is tolerant in opposition to any single fault, together with any single Byzantine fault. Should you lose your password, you have got a backup, which along with the server can recuperate your funds, and in case your password is hacked, the attacker solely has one password; likewise for loss or theft of the backup. If the service disappears, you have got two keys. If the service is hacked or seems to be evil, it solely has one. The chance of two failures occurring on the similar time may be very small; arguably, you usually tend to die.
Basic Models
All the above arguments make one key assumption that appears trivial, however really must be challenged far more carefully: that the elemental unit of the system is the pc. Every node has the inducement to mine on the block with the very best rating and never comply with some deviant technique. If the server will get hacked in a multisig then your laptop and your backup nonetheless have 2 out of three keys, so you might be nonetheless secure. The issue with the method is that it implicitly assumes that customers have full management over their computer systems, and that the customers totally perceive cryptography and are manually verifying the Merkle tree branches. In actuality, this isn’t the case; in truth, the very necessity of multisig in any incarnation in any respect is proof of this, because it acknowledges that customers’ computer systems can get hacked – a reproduction of the behavioral-economics concept that people will be seen as not being in full management of themselves.
A extra correct mannequin is to view a node as a mixture of two classes of brokers: a person, and a number of software program suppliers. Customers in practically all instances don’t confirm their software program; even in my very own case, despite the fact that I confirm each transaction that comes out of the Ethereum exodus tackle, utilizing the pybitcointools toolkit that I wrote from scratch myself (others have offered patches, however even these I reviewed personally), I’m nonetheless trusting that (1) the implementations of Python and Ubuntu that I downloaded are official, and (2) that the {hardware} isn’t in some way bugged. Therefore, these software program suppliers needs to be handled as separate entities, and their objectives and incentives needs to be analyzed as actors in their very own proper. In the meantime, customers also needs to be seen as brokers, however as brokers who’ve restricted technical functionality, and whose alternative set typically merely consists of which software program packages to put in, and never exactly which protocol guidelines to comply with.
The primary, and most essential, remark is that the ideas of “Byzantine fault tolerance” and “single level of failure” needs to be seen in mild of such a distinction. In idea, multisig removes all single factors of failure from the cryptographic token administration course of. In follow, nevertheless, that isn’t the best way that multisig is normally offered. Proper now, most mainstream multisig wallets are net functions, and the entity offering the online utility is identical entity that manages the backup signing key. What this implies is that, if the pockets supplier does get hacked or does become evil, they really have management over two out of three keys – they have already got the primary one, and might simply seize the second just by making a small change to the client-side browser utility they ship to you each time you load the webpage.
In multisig pockets suppliers’ protection, companies like BitGo and GreenAddress do provide an API, permitting builders to make use of their key administration performance with out their interface in order that the 2 suppliers will be separate entities. Nonetheless, the significance of this type of separation is presently drastically underemphasized.
This perception applies equally effectively to provably truthful playing and proof of solvency. Explicit, such provably truthful protocols ought to have normal implementations, with open-source functions that may confirm proofs in a typical format and in a approach that’s straightforward to make use of. Companies like exchanges ought to then comply with these protocols, and ship proofs which will be verifies by these exterior instruments. If a service releases a proof that may solely be verified by its personal inside instruments, that isn’t a lot better than no proof in any respect – barely higher, since there’s a probability that dishonest will nonetheless be detected, however not by a lot.
Software program, Customers and Protocols
If we really do have two courses of entities, it will likely be useful to offer at the very least a tough mannequin of their incentives, in order that we might higher perceive how they’re more likely to act. Typically, from software program suppliers we are able to roughly anticipate the next objectives:
- Maximize revenue – within the heyday of proprietary software program licensing, this purpose was really straightforward to know: software program corporations maximize their earnings by having as many customers as attainable. The drive towards open-source and free-to-use software program extra just lately has very many benefits, however one drawback is that it now makes the profit-maximization evaluation far more tough. Now, software program corporations usually generate income via business value-adds, the defensibility of which generally includes creating proprietary walled-garden ecosystems. Even nonetheless, nevertheless, making one’s software program as helpful as attainable normally helps, at the very least when it would not intrude with a proprietary value-add.
- Altruism – altruists write software program to assist folks, or to assist understand some imaginative and prescient of the world.
- Maximize fame – as of late, writing open-source software program is commonly used as a approach of build up one’s resume, in order to (1) seem extra enticing to employers and (2) achieve the social connections to maximise potential future alternatives. Firms can even do that, writing free instruments to drive folks to their web site as a way to promote different instruments.
- Laziness – software program suppliers won’t write code in the event that they may help it. The principle consequence of this shall be an underinvestment in options that don’t profit their customers, however profit the ecosystem – like responding to requests for knowledge – except the software program ecosystem is an oligopoly.
- Not going to jail – this entails compliance with legal guidelines, which generally includes anti-features similar to requiring id verification, however the dominant impact of this motive is a disincentive in opposition to screwing one’s prospects over too blatantly (eg. stealing their funds).
Customers we won’t analyze by way of objectives however quite by way of a behavioral mannequin: customers choose software program packages from an out there set, obtain the software program, and select choices from inside that software program. Guiding elements in software program choice embody:
- Performance – what’s the utility (that is the economics jargon “utility”) can they derive from the choices that the software program offers?
- Ease of use – of explicit significance is the query of how shortly they’ll rise up and operating doing what they should do.
- Perceived legitimacy – customers usually tend to obtain software program from reliable or at the very least trustworthy-seeming entities.
- Salience – if a software program package deal is talked about extra typically, customers shall be extra more likely to go for it. A direct consequence is that the “official” model of a software program package deal has a big benefit over any forks.
- Ethical and ideological issues – customers would possibly favor open supply software program for its personal sake, reject purely parasitic forks, and many others.
As soon as customers obtain a chunk of software program, the principle bias that we are able to depend on is that customers will keep on with defaults even when it won’t profit them to; past that, we’ve got extra conventional biases similar to loss aversion, which we’ll focus on briefly later.
Now, allow us to present an instance of how this course of works in motion: BitTorrent. Within the BitTorrent protocol, customers can obtain information from one another a packet at a time in a decentralized vogue, however to ensure that one person to obtain a file there should be somebody importing (“seeding”) it – and that exercise isn’t incentivized. In actual fact, it carries non-negligible prices: bandwidth consumption, CPU useful resource consumption, copyright-related authorized danger (together with danger of getting one’s web connection shut down by one’s ISP, or maybe even a chance of lawsuit). And but folks nonetheless seed – vastly insufficiently, however they do.
Why? The state of affairs is defined completely by the two-layer mannequin: software program suppliers need to make their software program extra helpful, so that they embody the seeding performance by default, and customers are too lazy to show it off (and a few customers are intentionally altruistic, although the order-of-magnitude mismatch between willingness to torrent copyrighted content material and willingness to donate to artists does recommend that almost all contributors do not actually care). Message-sending in Bitcoin (ie. to knowledge requests like getblockheader and getrawtransaction) can also be altruistic but in addition equally explainable, as is the inconsistency between transaction charges and what the economics recommend transaction charges presently needs to be.
One other instance is proof of stake algorithms. Proof of stake algorithms have the (principally) frequent vulnerability that there’s “nothing at stake” – that’s to say, that the default conduct within the occasion of a fork is to attempt to vote on all chains, so an attacker want solely overpower all altruists that vote on one chain solely, and never all altruists plus all rational actors as within the case of proof of labor. Right here, as soon as once more we are able to see that this doesn’t imply that proof of stake is totally damaged. If the stake is essentially managed by a smaller variety of subtle events, then these events may have their possession within the foreign money as the inducement to not take part in forks, and if the stake is managed by very many extra atypical folks then there would have to be some intentionally evil software program supplier who would take an effort to incorporate a multi-voting function, and promote it in order that probably customers really know in regards to the function.
Nonetheless, if the stake is held in custodial wallets (eg. Coinbase, Xapo, and many others) which don’t legally personal the cash, however are specialised skilled entities, then this argument breaks down: they’ve the technical capability to multi-vote, and low incentive to not, significantly if their companies should not “Bitcoin-centric” (or Ethereum-centric, or Ripple-cetric) and help many protocols. There may be even a probabilistic multi-voting technique which such custodial entities can use to get 99% of the advantages of multi-voting with out the chance of getting caught. Therefore, efficient proof of stake to a average extent relies on applied sciences that enable customers to soundly preserve management of their very own cash.
Darker Penalties
What we get out of the default impact is actually a sure degree of centralization, having a helpful position by setting customers’ default conduct towards a socially helpful motion and thereby correcting for what would in any other case be a market failure. Now, if software program introduces some advantages of centralization, we are able to additionally anticipate a few of the damaging results of centralization as effectively. One explicit instance is fragility. Theoretically, Bitcoin mining is an M-of-N protocol the place N is within the hundreds; in the event you do the combinatoric math, the chance that even 5% of the nodes will deviate from the protocol is infinitesimally small, so Bitcoin ought to have just about good reliability. In actuality, after all, that is incorrect; Bitcoin has had a minimum of two outages within the final six years.
For individuals who don’t bear in mind, the 2 instances have been as follows:

Driver of 43-year-old automobile exploits integer overflow vulnerability, sells it for 91% of authentic buy worth passing it off as new
- In 2010, an unknown person created a transaction with two outputs, every containing barely greater than 263 satoshis. The 2 outputs mixed have been barely over 264, and integer overflow led to the overall wrapping round to near-zero, inflicting the Bitcoin shopper to assume that the transaction really launched solely the identical small amount of BTC that it consumed as an enter, and so was official. The bug was fastened, and the blockchain reverted, after 9 hours.
- In 2013, a brand new model of the Bitcoin shopper unknowingly fastened a bug through which a block that remodeled 5000 accesses to a sure database useful resource would trigger a BerkeleyDB error, resulting in the shopper rejecting the block. Such a block quickly appeared, and new shoppers accepted it and previous shoppers rejected it, resulting in a fork. The fork was fastened in six hours, however within the meantime $10000 of BTC was stolen from a cost service supplier in a double-spend assault.
In each instances, the community was solely capable of fail as a result of, despite the fact that there have been hundreds of nodes, there was just one software program implementation operating all of them – maybe the final word fragility in a community that’s typically touted for being antifragile. Various implementations similar to btcd at the moment are more and more getting used, however it will likely be years earlier than Bitcoin Core’s monopoly is something near damaged; and even then fragility will nonetheless be pretty excessive.
Endowment results and Defaults
An essential set of biases to remember on the person facet are the ideas of the endowment impact, loss aversion, and the default impact. The three typically go hand in hand, however are considerably completely different from one another. The default impact is usually most precisely modeled as an inclination to proceed following one’s present technique except there’s a substantial profit to switching – in essence, a synthetic psychological switching value of some value ε. The endowment impact is the tendency to see issues as being extra precious if one already has them, and loss aversion is the tendency to care extra about avoiding losses than in search of features – experimentally, the scaling issue appears to be constantly round 2x.
The implications of those results pronounce themselves most strongly within the context of multi-currency environments. As one instance, contemplate the case of staff being paid in BTC. We are able to see that when persons are paid in BTC, they’re much extra more likely to maintain on to these BTC than they’d have been probably to purchase the BTC had they been paid USD; the reason being partially the default impact, and partially the truth that if somebody is paid in BTC they “assume in BTC” so in the event that they promote to USD then if the worth of BTC goes up after that they’ve a danger of struggling a loss, whereas if somebody is paid in USD it’s the USD-value of their BTC that they’re extra involved with. This is applicable additionally to smaller token techniques; in the event you pay somebody in Zetacoin, they’re more likely to money out into BTC or another coin, however the chance is far lower than 100%.
The loss aversion and default results are a few of the strongest arguments in favor of the thesis {that a} extremely polycentric foreign money system is more likely to proceed to outlive, contra Daniel Krawisz’s viewpoint that BTC is the one token to rule them all. There may be clearly an incentive for software program builders to create their very own coin even when the protocol might work simply as effectively on prime of an present foreign money: you are able to do a token sale. StorJ is the most recent instance of this. Nonetheless, as Daniel Krawisz argues, one might merely fork such an “app-coin” and launch a model on prime of Bitcoin, which might theoretically be superior as a result of Bitcoin is a extra liquid asset to retailer one’s funds in. The rationale why such an consequence has a big probability of not occurring is just the truth that customers comply with defaults, and by default customers will use StorJ with StorJcoin since that’s what the shopper will promote, and the unique StorJ shopper and web site and ecosystem is the one that may get all the eye.
Now, this argument breaks down considerably in a single case: if the fork is itself backed by a robust entity. The most recent instance of that is the case of Ripple and Stellar; though Stellar is a fork of Ripple, it’s backed by a big firm, Stripe, so the truth that the unique model of a software program package deal has the benefit of a lot higher salience doesn’t apply fairly as strongly. In such instances, we don’t actually know what’s going to occur; maybe, as is commonly the case within the social sciences, we’ll merely have to attend for empirical proof to seek out out.
The Means Ahead
Counting on particular psychological options of people in cryptographic protocol design is a harmful recreation. The rationale why it’s good in economics to maintain one’s mannequin easy, and in cryptoeconomics much more so, is that even when needs like the need to amass extra foreign money models don’t precisely describe the entire of human motivation, they describe an evidently very highly effective part of it, and a few might argue the one highly effective part we are able to depend on. Sooner or later, training might start to intentionally assault what we all know as psychological irregularities (in truth, it already does), altering tradition might result in altering morals and beliefs, and significantly on this case the brokers we’re coping with are “fyborgs” – useful cyborgs, or people who’ve all of their actions mediated by machines just like the one which sits between them and the web.
Nonetheless, there are specific basic options of this mannequin – the idea of cryptoeconomic techniques as two-layer techniques that includes software program and customers as brokers, the desire for simplicity, and many others, that maybe will be counted on, and on the very least we must always attempt to concentrate on circumstances the place our protocol is safe underneath the BAR mannequin, however insecure underneath the mannequin the place a couple of centralized events are in follow mediating everybody’s entry to the system. The mannequin additionally highlights the significance of “software program politics” – having an understanding of the pressures that drive software program improvement, and trying to provide you with approaches to improvement that software program builders have the very best incentives (or, finally, write software program that’s most favorable to the protocol’s profitable execution). These are issues that Bitcoin has not solved, and that Ethereum has not solved; maybe some future system will do at the very least considerably higher.
