Particular because of Vlad Zamfir and Zack Hess for ongoing analysis and discussions on proof-of-stake algorithms and their very own enter into Slasher-like proposals
One of many hardest problems in cryptocurrency growth is that of devising efficient consensus algorithms. Definitely, comparatively satisfactory default choices exist. On the very least it’s doable to depend on a Bitcoin-like proof of labor algorithm primarily based on both a randomly-generated circuit approach focused for specialized-hardware resitance, or failing that straightforward SHA3, and our existing GHOST optimizations enable for such an algorithm to offer block occasions of 12 seconds. Nonetheless, proof of labor as a normal class has many flaws that decision into query its sustainability as an unique supply of consensus; 51% assaults from altcoin miners, eventual ASIC dominance and excessive vitality inefficiency are maybe probably the most distinguished. Over the previous couple of months we’ve turn out to be increasingly satisfied that some inclusion of proof of stake is a crucial element for long-term sustainability; nonetheless, really implementing a proof of stake algorithm that’s efficient is proving to be surprisingly complex.
The truth that Ethereum features a Turing-complete contracting system complicates issues additional, because it makes sure sorts of collusion a lot simpler with out requiring belief, and creates a big pool of stake within the arms of decentralized entities which have the motivation to vote with the stake to gather rewards, however that are too silly to inform good blockchains from unhealthy. What the remainder of this text will present is a set of methods that cope with many of the points surrounding proof of stake algorithms as they exist right this moment, and a sketch of learn how to lengthen our present most well-liked proof-of-stake algorithm, Slasher, into one thing far more strong.
Historic Overview: Proof of stake and Slasher
If you happen to’re not but well-versed within the nuances of proof of stake algorithms, first learn: https://blog.ethereum.org/2014/07/05/stake/
The elemental drawback that consensus protocols attempt to clear up is that of making a mechanism for rising a blockchain over time in a decentralized means that can’t simply be subverted by attackers. If a blockchain doesn’t use a consensus protocol to manage block creation, and easily permits anybody so as to add a block at any time, then an attacker or botnet with very many IP addresses might flood the community with blocks, and notably they’ll use their energy to carry out double-spend assaults – sending a cost for a product, ready for the cost to be confirmed within the blockchain, after which beginning their very own “fork” of the blockchain, substituting the cost that they made earlier with a cost to a unique account managed by themselves, and rising it longer than the unique so everybody accepts this new blockchain with out the cost as fact.
The final resolution to this drawback entails making a block “onerous” to create in some vogue. Within the case of proof of labor, every block requires computational effort to provide, and within the case of proof of stake it requires possession of cash – normally, it is a probabilistic course of the place block-making privileges are doled out randomly in proportion to coin holdings, and in additional unique “destructive block reward” schemes anybody can create a block by spending a sure amount of funds, and they’re compensated through transaction charges. In any of those approaches, every chain has a “rating” that roughly displays the overall issue of manufacturing the chain, and the highest-scoring chain is taken to signify the “fact” at that exact time.
For an in depth overview of a few of the finer factors of proof of stake, see the above-linked article; for these readers who’re already conscious of the problems I’ll begin off by presenting a semi-formal specification for Slasher:
- Blocks are produced by miners; to ensure that a block to be legitimate it should fulfill a proof-of-work situation. Nonetheless, this situation is comparatively weak (eg. we will goal the mining reward to one thing like 0.02x the genesis provide yearly)
- Each block has a set of designated signers, that are chosen beforehand (see beneath). For a block with legitimate PoW to be accepted as a part of the chain it should be accompanied by signatures from at the least two thirds of its designated signers.
- When block N is produced, we are saying that the set of potential signers of block N + 3000 is the set of addresses such that sha3(handle + block[N].hash) < block[N].steadiness(handle) * D2 the place D2 is an issue parameter focusing on 15 signers per block (ie. if block N has lower than 15 signers it goes down in any other case it goes up). Word that the set of potential signers could be very computationally intensive to completely enumerate, and we do not strive to take action; as an alternative we depend on signers to self-declare.
- If a possible signer for block N + 3000 needs to turn out to be a chosen signer for that block, they need to ship a particular transaction accepting this duty and that transaction should get included between blocks N + 1 and N + 64. The set of designated signers for block N + 3000 is the set of all people that do that. This “signer should verify” mechanism helps guarantee that almost all of signers will really be on-line when the time involves signal. For blocks 0 … 2999, the set of signers is empty, so proof of labor alone suffices to create these blocks.
- When a chosen signer provides their signature to dam N + 3000, they’re scheduled to obtain a reward in block N + 6000.
- If a signer indicators two completely different blocks at peak N + 3000, then if somebody detects the double-signing earlier than block N + 6000 they’ll submit an “proof” transaction containing the 2 signatures, destroying the signer’s reward and transferring a 3rd of it to the whistleblower.
- If there may be an inadequate variety of signers to signal at a specific block peak h, a miner can produce a block with peak h+1 straight on high of the block with peak h-1 by mining at an 8x increased issue (to incentivize this, however nonetheless make it much less enticing than making an attempt to create a standard block, there’s a 6x increased reward). Skipping over two blocks has increased components of 16x diff and 12x reward, three blocks 32x and 24x, and so on.
Primarily, by explicitly punishing double-signing, Slasher in a whole lot of methods, though not all, makes proof of stake act like a type of simulated proof of labor. An necessary incidental advantage of Slasher is the non-revert property. In proof of labor, generally after one node mines one block another node will instantly mine two blocks, and so some nodes might want to revert again one block upon seeing the longer chain. Right here, each block requires two thirds of the signers to ratify it, and a signer can’t ratify two blocks on the similar peak with out dropping their beneficial properties in each chains, so assuming no malfeasance the blockchain won’t ever revert. From the viewpoint of a decentralized software developer, it is a very fascinating property because it signifies that “time” solely strikes in a single path, identical to in a server-based setting.
Nonetheless, Slasher continues to be weak to 1 specific class of assault: long-range assaults. As a substitute of making an attempt to begin a fork from ten blocks behind the present head, suppose that an attacker tries to begin a fork ranging from ten thousand blocks behind, and even the genesis block – all that issues is that the depth of the fork should be larger than the length of the reward lockup. At that time, as a result of customers’ funds are unlocked they usually can transfer them to a brand new handle to flee punishment, customers haven’t any disincentive in opposition to signing on each chains. In reality, we might even count on to see a black market of individuals promoting their previous non-public keys, culminating with an attacker single-handedly buying entry to the keys that managed over 50% of the forex provide in some unspecified time in the future in historical past.
One strategy to fixing the long-range double-signing drawback is transactions-as-proof-of-stake, an alternate PoS resolution that doesn’t have an incentive to double-sign as a result of it is the transactions that vote, and there’s no reward for sending a transaction (actually there is a price, and the reward is outdoors the community); nonetheless, this does nothing to cease the black key market drawback. To correctly cope with that problem, we might want to calm down a hidden assumption.
Subjective Scoring and Belief
For all its faults, proof of labor does have some elegant financial properties. Significantly, as a result of proof of labor requires an externally rivalrous useful resource, one thing with exists and is consumed outdoors the blockchain, so as to generate blocks (specifically, computational effort), launching a fork in opposition to a proof of labor chain invariably requires accessing, and spending, a big amount of financial sources. Within the case of proof of stake, then again, the one scarce worth concerned is worth throughout the chain, and between a number of chains that worth isn’t scarce in any respect. It doesn’t matter what algorithm is used, in proof of stake 51% of the homeowners of the genesis block might ultimately come collectively, collude, and produce an extended (ie. higher-scoring) chain than everybody else.
This will appear to be a deadly flaw, however in actuality it is just a flaw if we implicitly settle for an assumption that’s made within the case of proof of labor: that nodes haven’t any data of historical past. In a proof-of-work protocol, a brand new node, having no direct data of previous occasions and seeing nothing however the protocol supply code and the set of messages which have already been revealed, can be part of the community at any level and decide the rating of all doable chains, and from there the block that’s on the high of the highest-scoring foremost chain. With proof of stake, as we described, such a property can’t be achieved, since it’s totally low-cost to amass historic keys and simulate alternate histories. Thus, we’ll calm down our assumptions considerably: we’ll say that we’re solely involved with sustaining consensus between a static set of nodes which might be on-line at the least as soon as each N days, permitting these nodes to make use of their very own data of historical past to reject apparent long-range forks utilizing some method, and new nodes or long-dormant nodes might want to specify a “checkpoint” (a hash of a block representing what the remainder of the community agrees is a latest state) so as to get again onto the consensus.
Such an strategy is basically a hybrid between the pure and maybe harsh trust-no-one logic of Bitcoin and the overall dependency on socially-driven consensus present in networks like Ripple. In Ripple’s case, customers becoming a member of the system want to pick out a set of nodes that they belief (or, extra exactly, belief to not collude) and depend on these nodes throughout each step of the consensus course of. Within the case of Bitcoin, the speculation is that no such belief is required and the protocol is totally self-contained; the system works simply as properly between a thousand remoted cavemen with laptops on a thousand islands because it does in a strongly related society (actually, it’d work higher with island cavemen, since with out belief collusion is tougher). In our hybrid scheme, customers want solely look to the society outdoors of the protocol precisely as soon as – once they first obtain a shopper and discover a checkpoint – and might take pleasure in Bitcoin-like belief properties ranging from that time.
With a purpose to decide which belief assumption is the higher one to take, we in the end have to ask a considerably philosophical query: do we would like our consensus protocols to exist as absolute cryptoeconomic constructs utterly impartial of the skin world, or are we okay with relying closely on the truth that these methods exist within the context of a wider society? Though it’s certainly a central tenet of mainstream cryptocurrency philosophy that an excessive amount of exterior dependence is harmful, arguably the extent of independence that Bitcoin affords us in actuality isn’t any larger than that offered by the hybrid mannequin. The argument is straightforward: even within the case of Bitcoin, a consumer should additionally take a leap of belief upon becoming a member of the community – first by trusting that they’re becoming a member of a protocol that accommodates property that different individuals discover worthwhile (eg. how does a consumer know that bitcoins are value $380 every and dogecoins solely $0.0004? Particularly with the completely different capabilities of ASICs for various algorithms, hashpower is just a really tough estimate), and second by trusting that they’re downloading the correct software package. In each the supposedly “pure” mannequin and the hybrid mannequin there may be all the time a have to look outdoors the protocol precisely as soon as. Thus, on the entire, the acquire from accepting the additional belief requirement (specifically, environmental friendliness and safety in opposition to oligopolistic mining pools and ASIC farms) is arguably value the price.
Moreover, we might notice that, in contrast to Ripple consensus, the hybrid mannequin continues to be suitable with the thought of blockchains “speaking” to every one another by containing a minimal “gentle” implementation of one another’s protocols. The reason being that, whereas the scoring mechanism isn’t “absolute” from the viewpoint of a node with out historical past out of the blue each block, it’s completely adequate from the viewpoint of an entity that is still on-line over an extended time period, and a blockchain actually is such an entity.
To this point, there have been two main approaches that adopted some type of checkpoint-based belief mannequin:
- Developer-issued checkpoints – the shopper developer points a brand new checkpoint with every shopper improve (eg. utilized in PPCoin)
- Revert restrict – nodes refuse to simply accept forks that revert greater than N (eg. 3000) blocks (eg. utilized in Tendermint)
The primary strategy has been roundly criticized by the cryptocurrency group for being too centralized. The second, nonetheless, additionally has a flaw: a strong attacker can’t solely revert a couple of thousand blocks, but additionally doubtlessly cut up the community completely. Within the N-block revert case, the technique is as follows. Suppose that the community is at the moment at block 10000, and N = 3000. The attacker begins a secret fork, and grows it by 3001 blocks sooner than the principle community. When the principle community will get to 12999, and a few node produces block 13000, the attacker reveals his personal fork. Some nodes will see the principle community’s block 13000, and refuse to modify to the attacker’s fork, however the nodes that didn’t but see that block will likely be pleased to revert from 12999 to 10000 after which settle for the attacker’s fork. From there, the community is completely cut up.
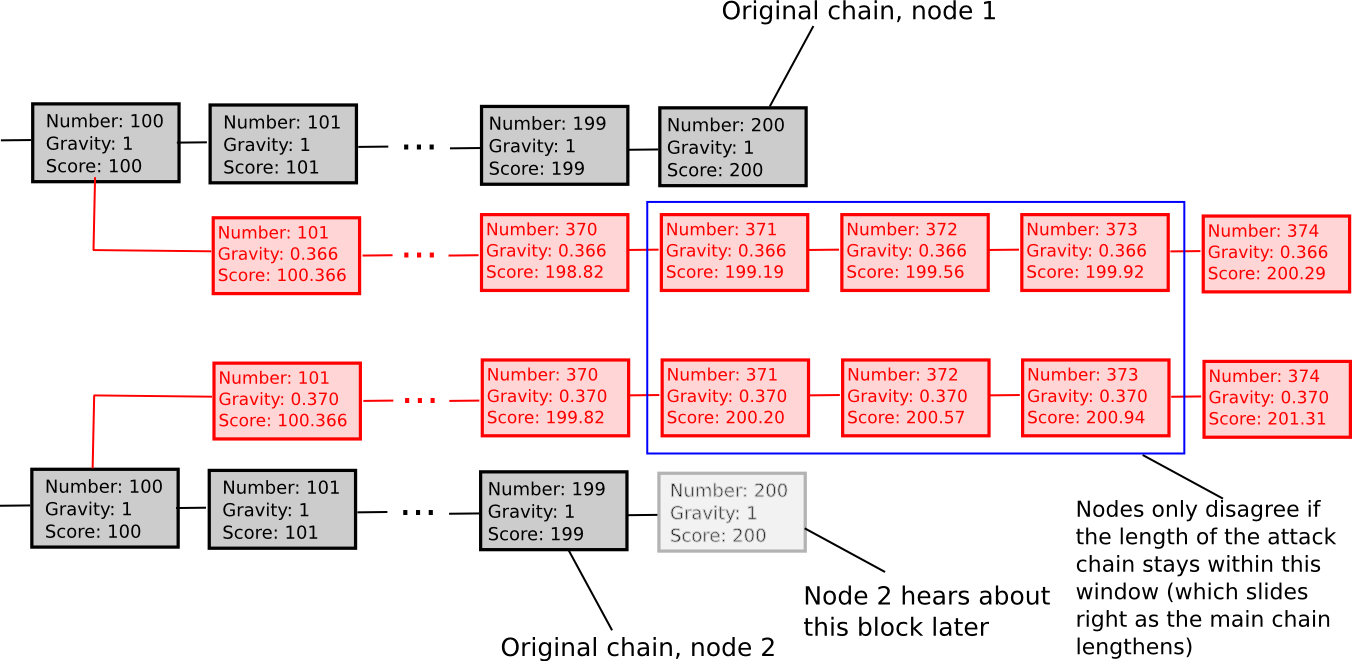
Luckily, one can really assemble a 3rd strategy that neatly solves this drawback, which we’ll name exponentially subjective scoring. Primarily, as an alternative of rejecting forks that return too far, we merely penalize them on a graduating scale. For each block, a node maintains a rating and a “gravity” issue, which acts as a multiplier to the contribution that the block makes to the blockchain’s rating. The gravity of the genesis block is 1, and usually the gravity of every other block is about to be equal to the gravity of its mum or dad. Nonetheless, if a node receives a block whose mum or dad already has a series of N descendants (ie. it is a fork reverting N blocks), that block’s gravity is penalized by an element of 0.99N, and the penalty propagates perpetually down the chain and stacks multiplicatively with different penalties.
That’s, a fork which begins 1 block in the past might want to develop 1% sooner than the principle chain so as to overtake it, a fork which begins 100 blocks in the past might want to develop 2.718 occasions as rapidly, and a fork which begins 3000 blocks in the past might want to develop 12428428189813 occasions as rapidly – clearly an impossibility with even trivial proof of labor.
The algorithm serves to clean out the position of checkpointing, assigning a small “weak checkpoint” position to every particular person block. If an attacker produces a fork that some nodes hear about even three blocks sooner than others, these two chains might want to keep inside 3% of one another perpetually to ensure that a community cut up to keep up itself.
There are different options that may very well be used apart from, and even alongside ESS; a specific set of methods entails stakeholders voting on a checkpoint each few thousand blocks, requiring each checkpoint produced to mirror a big consensus of the bulk of the present stake (the rationale nearly all of the stake cannot vote on each block is, in fact, that having that many signatures would bloat the blockchain).
Slasher Ghost
The opposite massive complexity in implementing proof of stake for Ethereum particularly is the truth that the community features a Turing-complete monetary system the place accounts can have arbitrary permissions and even permissions that change over time. In a easy forex, proof of stake is comparatively simple to perform as a result of every unit of forex has an unambiguous proprietor outdoors the system, and that proprietor will be counted on to take part within the stake-voting course of by signing a message with the non-public key that owns the cash. In Ethereum, nonetheless, issues are usually not fairly so easy: if we do our job selling correct pockets safety proper, nearly all of ether goes to be saved in specialised storage contracts, and with Turing-complete code there is no such thing as a clear means of ascertaining or assigning an “proprietor”.
One technique that we checked out was delegation: requiring each handle or contract to assign an handle as a delegate to signal for them, and that delegate account must be managed by a non-public key. Nonetheless, there’s a drawback with any such strategy. Suppose {that a} majority of the ether within the system is definitely saved in software contracts (versus private storage contracts); this consists of deposits in SchellingCoins and different stake-based protocols, safety deposits in probabilistic enforcement systems, collateral for monetary derivatives, funds owned by DAOs, and so on. These contracts shouldn’t have an proprietor even in spirit; in that case, the worry is that the contract will default to a method of renting out stake-voting delegations to the very best bidder. As a result of attackers are the one entities keen to bid greater than the anticipated return from the delegation, this may make it very low-cost for an attacker to amass the signing rights to massive portions of stake.
The one resolution to this throughout the delegation paradigm is to make it extraordinarily dangerous to dole out signing privileges to untrusted events; the only strategy is to change Slasher to require a big deposit, and slash the deposit in addition to the reward within the occasion of double-signing. Nonetheless, if we do that then we’re primarily again to entrusting the destiny of a giant amount of funds to a single non-public key, thereby defeating a lot of the purpose of Ethereum within the first place.
Luckily, there may be one various to delegation that’s considerably more practical: letting contracts themselves signal. To see how this works, contemplate the next protocol:
- There may be now a SIGN opcode added.
- A signature is a sequence of digital transactions which, when sequentially utilized to the state on the finish of the mum or dad block, leads to the SIGN opcode being referred to as. The nonce of the primary VTX within the signature should be the prevhash being signed, the nonce of the second should be the prevhash plus one, and so forth (alternatively, we will make the nonces -1, -2, -3 and so on. and require the prevhash to be handed in by transaction knowledge in order to be ultimately provided as an enter to the SIGN opcode).
- When the block is processed, the state transitions from the VTXs are reverted (that is what is supposed by “digital”) however a deposit is subtracted from every signing contract and the contract is registered to obtain the deposit and reward in 3000 blocks.
Mainly, it’s the contract’s job to find out the entry coverage for signing, and the contract does this by inserting the SIGN opcode behind the suitable set of conditional clauses. A signature now turns into a set of transactions which collectively fulfill this entry coverage. The motivation for contract builders to maintain this coverage safe, and never dole it out to anybody who asks, is that if it isn’t safe then somebody can double-sign with it and destroy the signing deposit, taking a portion for themselves as per the Slasher protocol. Some contracts will nonetheless delegate, however that is unavoidable; even in proof-of-stake methods for plain currencies similar to NXT, many customers find yourself delegating (eg. DPOS even goes as far as to institutionalize delegation), and at the least right here contracts have an incentive to delegate to an entry coverage that isn’t more likely to come underneath the affect of a hostile entity – actually, we might even see an equilibrium the place contracts compete to ship safe blockchain-based stake swimming pools which might be least more likely to double-vote, thereby rising safety over time.
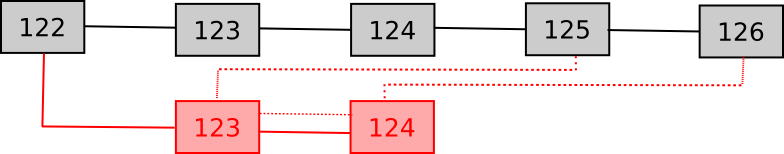
Nonetheless, the virtual-transactions-as-signatures paradigm does impose one complication: it’s not trivial to offer an proof transaction displaying two signatures by the identical signer on the similar block peak. As a result of the results of a transaction execution relies on the beginning state, so as to verify whether or not a given proof transaction is legitimate one should show the whole lot as much as the block through which the second signature was given. Thus, one should primarily “embody” the fork of a blockchain inside the principle chain. To do that effectively, a comparatively easy proposal is a type of “Slasher GHOST” protocol, the place one can embody side-blocks in the principle chain as uncles. Particularly, we declare two new transaction sorts:
- [block_number, uncle_hash] – this transaction is legitimate if (1) the block with the given uncle_hash has already been validated, (2) the block with the given uncle_hash has the given block quantity, and (3) the mum or dad of that uncle is both in the principle chain or was included earlier as an uncle. In the course of the act of processing this transaction, if addresses that double-signed at that peak are detected, they’re appropriately penalized.
- [block_number, uncle_parent_hash, vtx] – this transaction is legitimate if (1) the block with the given uncle_parent_hash has already been validated, (2) the given digital transaction is legitimate on the given block peak with the state on the finish of uncle_parent_hash, and (3) the digital transaction reveals a signature by an handle which additionally signed a block on the given block_number in the principle chain. This transaction penalizes that one handle.
Primarily, one can consider the mechanism as working like a “zipper”, with one block from the fork chain at a time being zipped into the principle chain. Word that for a fork to begin, there should exist double-signers at each block; there is no such thing as a state of affairs the place there’s a double-signer 1500 blocks right into a fork so a whistleblower should “zip” 1499 harmless blocks into a series earlier than attending to the goal block – quite, in such a case, even when 1500 blocks must be added, every one among them notifies the principle chain about 5 separate malfeasors that double-signed at that peak. One considerably difficult property of the scheme is that the validity of those “Slasher uncles” relies on whether or not or not the node has validated a specific block outdoors of the principle chain; to facilitate this, we specify {that a} response to a “getblock” message within the wire protocol should embody the uncle-dependencies for a block earlier than the precise block. Word that this will likely generally result in a recursive enlargement; nonetheless, the denial-of-service potential is proscribed since every particular person block nonetheless requires a considerable amount of proof-of-work to provide.
Blockmakers and Overrides
Lastly, there’s a third complication. Within the hybrid-proof-of-stake model of Slasher, if a miner has an amazing share of the hashpower, then the miner can produce a number of variations of every block, and ship completely different variations to completely different components of the community. Half the signers will see and signal one block, half will see and signal one other block, and the community will likely be caught with two blocks with inadequate signatures, and no signer keen to slash themselves to finish the method; thus, a proof-of-work override will likely be required, a harmful state of affairs because the miner controls many of the proof-of-work. There are two doable options right here:
- Signers ought to wait a couple of seconds after receiving a block earlier than signing, and solely signal stochastically in some vogue that ensures {that a} random one of many blocks will dominate.
- There must be a single “blockmaker” among the many signers whose signature is required for a block to be legitimate. Successfully, this transfers the “management” position from a miner to a stakeholder, eliminating the issue, however at the price of including a dependency on a single social gathering that now has the power to considerably inconvenience everybody by not signing, or unintentionally by being the goal of a denial-of-service assault. Such habits will be disincentivized by having the signer lose a part of their deposit if they don’t signal, however even nonetheless this may end in a quite jumpy block time if the one solution to get round an absent blockmaker is utilizing a proof-of-work override.
One doable resolution to the issue in (2) is to take away proof of labor solely (or virtually solely, retaining a minimal quantity for anti-DDoS worth), changing it with a mechanism that Vlad Zamfir has coined “delegated timestamping”. Primarily, each block should seem on schedule (eg. at 15 second intervals), and when a block seems the signers vote 1 if the block was on time, or 0 if the block was too early or too late. If nearly all of the signers votes 0, then the block is handled as invalid – saved within the chain so as to give the signers their truthful reward, however the blockmaker will get no reward and the state transition will get passed over. Voting is incentivized through schellingcoin – the signers whose vote agrees with the bulk get an additional reward, so assuming that everybody else goes to be sincere everybody has the motivation to be sincere, in a self-reinforcing equilibrium. The speculation is {that a} 15-second block time is simply too quick for signers to coordinate on a false vote (the astute reader might notice that the signers had been determined 3000 blocks upfront so this isn’t actually true; to repair this we will create two teams of signers, one pre-chosen group for validation and one other group chosen at block creation time for timestamp voting).
Placing all of it Collectively
Taken collectively, we will thus see one thing like the next working as a purposeful model of Slasher:
- Each block has a designated blockmaker, a set of designated signers, and a set of designated timestampers. For a block to be accepted as a part of the chain it should be accompanied by virtual-transactions-as-signatures from the blockmaker, two thirds of the signers and 10 timestampers, and the block will need to have some minimal proof of labor for anti-DDoS causes (say, focused to 0.01x per yr)
- Throughout block N, we are saying that the set of potential signers of block N + 3000 is the set of addresses such that sha3(handle + block[N].hash) < block[N].steadiness(handle) * D2 the place D2 is an issue parameter focusing on 15 signers per block (ie. if block N has lower than 15 signers it goes down in any other case it goes up).
- If a possible signer for block N + 3000 needs to turn out to be a signer, they need to ship a particular transaction accepting this duty and supplying a deposit, and that transaction should get included between blocks N + 1 and N + 64. The set of designated signers for block N + 3000 is the set of all people that do that, and the blockmaker is the designated signer with the bottom worth for sha3(handle + block[N].hash). If the signer set is empty, no block at that peak will be made. For blocks 0 … 2999, the blockmaker and solely signer is the protocol developer.
- The set of timestampers of the block N + 3000 is the set of addresses such that sha3(handle + block[N].hash) < block[N].steadiness(handle) * D3, the place D3 is focused such that there’s a mean of 20 timestampers every block (ie. if block N has lower than 20 timestampers it goes down in any other case it goes up).
- Let T be the timestamp of the genesis block. When block N + 3000 is launched, timestampers can provide virtual-transactions-as-signatures for that block, and have the selection of voting 0 or 1 on the block. Voting 1 signifies that they noticed the block inside 7.5 seconds of time T + (N + 3000) * 15, and voting 0 signifies that they obtained the block when the time was outdoors that vary. Word that nodes ought to detect if their clocks are out of sync with everybody else’s clocks on the blockchain, and if that’s the case regulate their system clocks.
- Timestampers who voted together with the bulk obtain a reward, different timestampers get nothing.
- The designated signers for block N + 3000 have the power to signal that block by supplying a set of virtual-transactions-as-a-signature. All designated signers who signal are scheduled to obtain a reward and their returned deposit in block N + 6000. Signers who skipped out are scheduled to obtain their returned deposit minus twice the reward (which means that it is solely economically worthwhile to enroll as a signer if you happen to really assume there’s a probability larger than 2/3 that you can be on-line).
- If the bulk timestamper vote is 1, the blockmaker is scheduled to obtain a reward and their returned deposit in block N + 6000. If the bulk timestamper vote is 0, the blockmaker is scheduled to obtain their deposit minus twice the reward, and the block is ignored (ie. the block is within the chain, however it doesn’t contribute to the chain’s rating, and the state of the subsequent block begins from the top state of the block earlier than the rejected block).
- If a signer indicators two completely different blocks at peak N + 3000, then if somebody detects the double-signing earlier than block N + 6000 they’ll submit an “proof” transaction containing the 2 signatures to both or each chains, destroying the signer’s reward and deposit and transferring a 3rd of it to the whistleblower.
- If there may be an inadequate variety of signers to signal or the blockmaker is lacking at a specific block peak h, the designated blockmaker for peak h + 1 can produce a block straight on high of the block at peak h – 1 after ready for 30 seconds as an alternative of 15.
After years of analysis, one factor has turn out to be clear: proof of stake is non-trivial – so non-trivial that some even consider it impossible. The problems of nothing-at-stake and long-range assaults, and the dearth of mining as a rate-limiting machine, require a variety of compensatory mechanisms, and even the protocol above doesn’t handle the difficulty of learn how to randomly choose signers. With a considerable proof of labor reward, the issue is proscribed, as block hashes is usually a supply of randomness and we will mathematically present that the acquire from holding again block hashes till a miner finds a hash that favorably selects future signers is often lower than the acquire from publishing the block hashes. With out such a reward, nonetheless, different sources of randomness similar to low-influence features must be used.
For Ethereum 1.0, we contemplate it extremely fascinating to each not excessively delay the discharge and never strive too many untested options directly; therefore, we’ll possible keep on with ASIC-resistant proof of labor, maybe with non-Slasher proof of activity as an addon, and have a look at transferring to a extra complete proof of stake mannequin over time.