Blockchains are a robust know-how, as common readers of the weblog already probably agree. They permit for numerous interactions to be codified and carried out in a method that significantly will increase reliability, removes enterprise and political dangers related to the method being managed by a central entity, and reduces the necessity for belief. They create a platform on which functions from totally different firms and even of various varieties can run collectively, permitting for very environment friendly and seamless interplay, and go away an audit path that anybody can examine to be sure that all the pieces is being processed accurately.
Nonetheless, after I and others speak to firms about constructing their functions on a blockchain, two main points at all times come up: scalability and privateness. Scalability is a major problem; present blockchains, processing 3-20 transactions per second, are a number of orders of mangitude away from the quantity of processing energy wanted to run mainstream cost methods or monetary markets, a lot much less decentralized boards or international micropayment platforms for IoT. Thankfully, there are solutions, and we’re actively engaged on implementing a roadmap to creating them occur. The opposite main drawback that blockchains have is privateness. As seductive as a blockchain’s different benefits are, neither firms or people are notably eager on publishing all of their info onto a public database that may be arbitrarily learn with none restrictions by one’s personal authorities, overseas governments, relations, coworkers and enterprise opponents.
Not like with scalability, the options for privateness are in some circumstances simpler to implement (although in different circumstances a lot a lot more durable), lots of them appropriate with presently present blockchains, however they’re additionally a lot much less satisfying. It is a lot more durable to create a “holy grail” know-how which permits customers to do completely all the pieces that they’ll do proper now on a blockchain, however with privateness; as an alternative, builders will in lots of circumstances be pressured to deal with partial options, heuristics and mechanisms which can be designed to convey privateness to particular lessons of functions.
The Holy Grail
First, allow us to begin off with the applied sciences that are holy grails, in that they really do provide the promise of changing arbitrary functions into absolutely privacy-preserving functions, permitting customers to profit from the safety of a blockchain, utilizing a decentralized community to course of the transactions, however “encrypting” the info in such a method that although all the pieces is being computed in plain sight, the underlying “which means” of the knowledge is totally obfuscated.
Probably the most highly effective know-how that holds promise in course is, in fact, cryptographically safe obfuscation. Basically, obfuscation is a method of turning any program right into a “black field” equal of this system, in such a method that this system nonetheless has the identical “inner logic”, and nonetheless provides the identical outputs for a similar inputs, but it surely’s unimaginable to find out another particulars about how this system works.
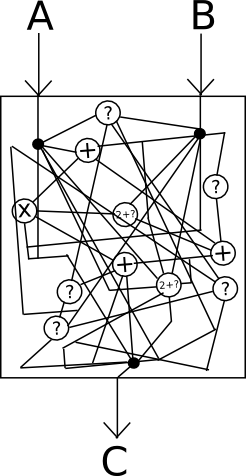
Consider it as “encrypting” the wires within the field in such a method that the encryption cancels itself out and in the end has no impact on the output, however does have the impact of creating it completely unimaginable to see what’s going on inside.
Sadly, completely good black-box obfuscation is mathematically known to be impossible; it seems that there’s at all times at the very least one thing that you would be able to get extract out of a program by it past simply the outputs that it provides on a particular set of inputs. Nonetheless, there’s a weaker normal referred to as indistinguishability obfuscation that we will fulfill: basically, given two equal packages which were obfuscated utilizing the algorithm (eg. x = (a + b) * c and x = (a * c) + (b * c)), one can’t decide which of the 2 outputs got here from which unique supply. To see how that is nonetheless highly effective sufficient for our functions, think about the next two packages:
- y = 0
- y = signal(privkey, 0) – signal(privkey, 0)
One simply returns zero, and the opposite makes use of an internally contained personal key to cryptographically signal a message, does that very same operation one other time, subtracts the (clearly an identical) outcomes from one another and returns the outcome, which is assured to be zero. Regardless that one program simply returns zero, and the opposite incorporates and makes use of a cryptographic personal key, if indistinguishability is glad then we all know that the 2 obfuscated packages can’t be distinguished from one another, and so somebody in possession of the obfuscated program undoubtedly has no method of extracting the personal key – in any other case, that may be a method of distinguishing the 2 packages. That is some fairly highly effective obfuscation proper there – and for about two years we have recognized easy methods to do it!
So, how will we use this on a blockchain? This is one easy method for a digital token. We create an obfuscated sensible contract which incorporates a personal key, and accepts directions encrypted with the correponding public key. The contract shops account balances in storage encrypted, and if the contract desires to learn the storage it decrypts it internally, and if the contract desires to write down to storage it encrypts the specified outcome earlier than writing it. If somebody desires to learn a steadiness of their account, then they encode that request as a transaction, and simulate it on their very own machine; the obfuscated sensible contract code will examine the signature on the transaction to see if that consumer is entitled to learn the steadiness, and if they’re entitled to learn the steadiness it would return the decrypted steadiness; in any other case the code will return an error, and the consumer has no method of extracting the knowledge.
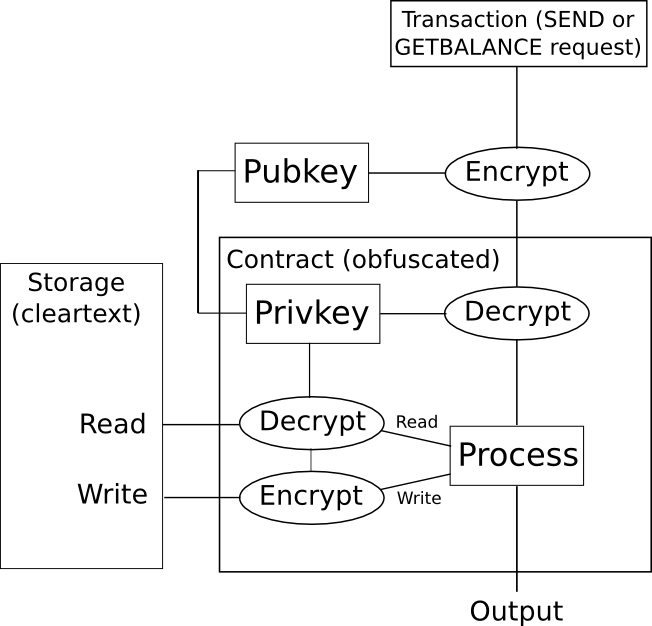
Nonetheless, as with a number of different applied sciences of this sort, there’s one drawback: the mechanism for doing this sort of obfuscation is horrendously inefficient. Billion-factor overhead is the norm, and sometimes even extremely optimistic; a recent paper estimates that “executing [a 2-bit multiplication] circuit on the identical CPU would take 1.3 * 108 years”. Moreover, if you wish to stop reads and writes to storage from being a knowledge leak vector, you could additionally arrange the contract in order that learn and write operations at all times modify giant parts of a contract’s whole state – one other supply of overhead. When, on high of that, you’ve got the overhead of a whole bunch of nodes working the code on a blockchain, one can shortly see how this know-how is, sadly, not going to vary something any time quickly.
Taking A Step Down
Nonetheless, there are two branches of know-how that may get you nearly so far as obfuscation, although with essential compromises to the safety mannequin. The primary is safe multi-party computation. Safe multi-party computation permits for a program (and its state) to be break up amongst N events in such a method that you simply want M of them (eg. N = 9, M = 5) to cooperate as a way to both full the computation or reveal any inner information in this system or the state. Thus, should you can belief the vast majority of the individuals to be trustworthy, the scheme is pretty much as good as obfuscation. If you cannot, then it is nugatory.
The maths behind safe multi-party computation is complicated, however a lot easier than obfuscation; in case you are within the technical particulars, then you’ll be able to learn extra here (and in addition the paper of Enigma, a venture that seeks to really implement the key sharing DAO idea, here). SMPC can also be rather more environment friendly than obfuscation, the purpose that you would be able to perform sensible computations with it, however even nonetheless the inefficiencies are very giant. Addition operations could be processed pretty shortly, however each time an SMPC occasion performs some very small mounted variety of multiplication operations it must carry out a “diploma discount” step involving messages being despatched from each node to each node within the community. Current work reduces the communication overhead from quadratic to linear, however even nonetheless each multiplication operation brings a sure unavoidable stage of community latency.
The requirement of belief on the individuals can also be an onerous one; observe that, as is the case with many different functions, the individuals have the power to avoid wasting the info after which collude to uncover at any future level in historical past. Moreover, it’s unimaginable to inform that they’ve finished this, and so it’s unimaginable to incentivize the individuals to take care of the system’s privateness; for that reason, safe multi-party computation is arguably rather more suited to non-public blockchains, the place incentives can come from outdoors the protocol, than public chains.
One other sort of know-how that has very highly effective properties is zero-knowledge proofs, and particularly the current developments in “succinct arguments of knowledge” (SNARKs). Zero-knowledge proofs enable a consumer to assemble a mathematical proof {that a} given program, when executed on some (presumably hidden) enter recognized by the consumer, has a selected (publicly recognized) output, with out revealing another info. There are various specialised sorts of zero-knowledge proofs which can be pretty straightforward to implement; for instance, you’ll be able to consider a digital signature as a sort of zero-knowledge proof exhibiting that you understand the worth of a personal key which, when processed utilizing a normal algorithm, could be transformed into a selected public key. ZK-SNARKs, however, let you make such a proof for any perform.
First, allow us to undergo some particular examples. One pure use case for the know-how is in id methods. For instance, suppose that you simply wish to show to a system that you’re (i) a citizen of a given nation, and (ii) over 19 years previous. Suppose that your authorities is technologically progressive, and points cryptographically signed digital passports, which embrace an individual’s identify and date of start in addition to a personal and public key. You’ll assemble a perform which takes a digital passport and a signature signed by the personal key within the passport as enter, and outputs 1 if each (i) the date of start is earlier than 1996, (ii) the passport was signed with the federal government’s public key, and (iii) the signature is appropriate, and outputs 0 in any other case. You’ll then make a zero-knowledge proof exhibiting that you’ve an enter that, when handed via this perform, returns 1, and signal the proof with one other personal key that you simply wish to use in your future interactions with this service. The service would confirm the proof, and if the proof is appropriate it will settle for messages signed together with your personal key as legitimate.
You possibly can additionally use the identical scheme to confirm extra complicated claims, like “I’m a citizen of this nation, and my ID quantity is just not on this set of ID numbers which have already been used”, or “I’ve had favorable evaluations from some retailers after buying at the very least $10,000 value of merchandise from them”, or “I maintain property value at the very least $250,000”.
One other class of use circumstances for the know-how is digital token possession. To be able to have a functioning digital token system, you don’t strictly have to have seen accounts and balances; the truth is, all that you simply want is a approach to remedy the “double spending” drawback – in case you have 100 items of an asset, it is best to be capable of spend these 100 items as soon as, however not twice. With zero-knowledge proofs, we will in fact do that; the declare that you’d zero-knowledge-prove is one thing like “I do know a secret quantity behind one of many accounts on this set of accounts which were created, and it doesn’t match any of the key numbers which have already been revealed”. Accounts on this scheme develop into one-time-use: an “account” is created each time property are despatched, and the sender account is totally consumed. If you don’t want to fully eat a given account, then you could merely create two accounts, one managed by the recipient and the opposite with the remaining “change” managed by the sender themselves. That is basically the scheme utilized by Zcash (see extra about the way it works here).
For 2-party sensible contracts (eg. consider one thing like a monetary by-product contract negotiated between two events), the applying of zero-knowledge-proofs is pretty straightforward to grasp. When the contract is first negotiated, as an alternative of making a sensible contract containing the precise system by which the funds will ultimately be launched (eg. in a binary possibility, the system could be “if index I as launched by some information supply is larger than X, ship all the pieces to A, in any other case ship all the pieces to B”), create a contract containing the hash of the system. When the contract is to be closed, both celebration can themselves compute the quantity that A and B ought to obtain, and supply the outcome alongside a zero-knowledge-proof {that a} system with the proper hash supplies that outcome. The blockchain finds out how a lot A and B every put in, and the way a lot they get out, however not why they put in or get out that quantity.
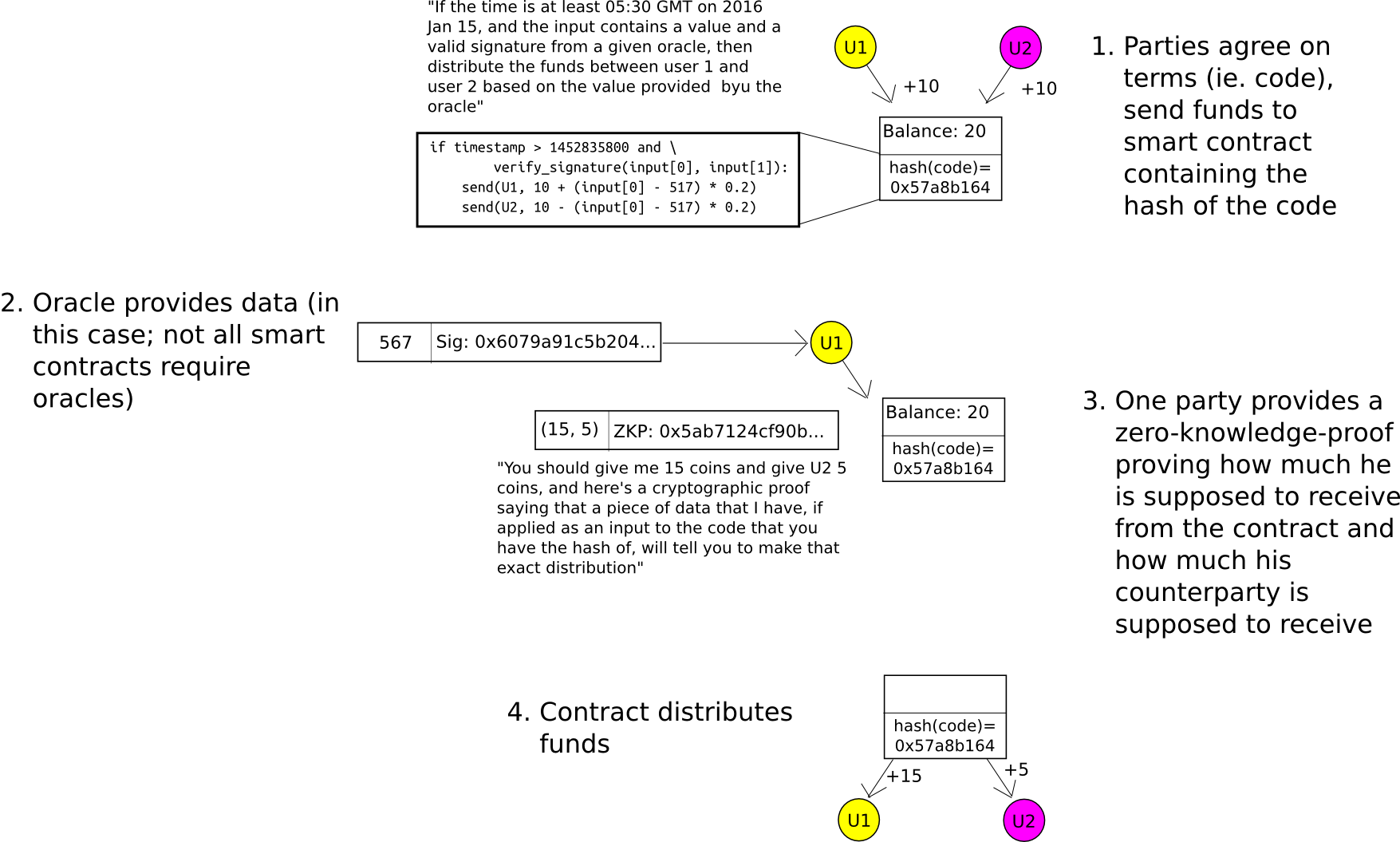
This mannequin could be generalized to N-party sensible contracts, and the Hawk venture is searching for to do precisely that.
Ranging from the Different Finish: Low-Tech Approaches
The opposite path to take when making an attempt to extend privateness on the blockchain is to begin with very low-tech approaches, utilizing no crypto past easy hashing, encryption and public key cryptography. That is the trail that Bitcoin began from in 2009; although the extent of privateness that it supplies in observe is kind of tough to quantify and restricted, it nonetheless clearly supplied some worth.
The only step that Bitcoin took to considerably improve privateness is its use of one-time accounts, much like Zcash, as a way to retailer funds. Similar to with Zcash, each transaction should fully empty a number of accounts, and create a number of new accounts, and it’s endorsed for customers to generate a brand new personal key for each new account that they intend to obtain funds into (although it’s doable to have a number of accounts with the identical personal key). The primary profit that this brings is {that a} consumer’s funds usually are not linked to one another by default: should you obtain 50 cash from supply A and 50 cash from supply B, there is no such thing as a method for different customers to inform that these funds belong to the identical individual. Moreover, should you spend 13 cash to another person’s account C, and thereby create a fourth account D the place you ship the remaining 37 cash from one among these accounts as “change”, the opposite customers can’t even inform which of the 2 outputs of the transaction is the “cost” and which is the “change”.
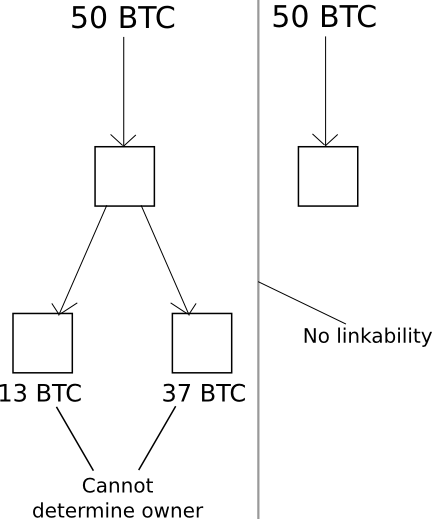
Nonetheless, there’s a drawback. If, at any level sooner or later, you make a transaction consuming from two accounts on the identical time, then you definately irrevertibly “hyperlink” these accounts, making it apparent to the world that they arrive from one consumer. And, what’s extra, these linkages are transitive: if, at any level, you hyperlink collectively A and B, after which at another level hyperlink collectively A and C, and so forth, then you definately’ve created a considerable amount of proof by which statistical evaluation can hyperlink up your whole set of property.

Bitcoin developer Mike Hearn got here up with a mitigation technique that reduces the probability of this occurring referred to as merge avoidance: basically, a flowery time period for making an attempt actually actually arduous to attenuate the variety of occasions that you simply hyperlink accounts collectively by spending from them on the identical time. This undoubtedly helps, however even nonetheless, privateness within the Bitcoin system has confirmed to be extremely porous and heuristic, with nothing even near approaching excessive ensures.
A considerably extra superior method known as CoinJoin. Primarily, the CoinJoin protocol works as follows:
- N events come collectively over some nameless channel, eg. Tor. They every present a vacation spot deal with D[1] … D[N].
- One of many events creates a transaction which sends one coin to every vacation spot deal with.
- The N events log off after which individually log in to the channel, and every contribute one coin to the account that the funds can be paid out from.
- If N cash are paid into the account, they’re distributed to the vacation spot addresses, in any other case they’re refunded.
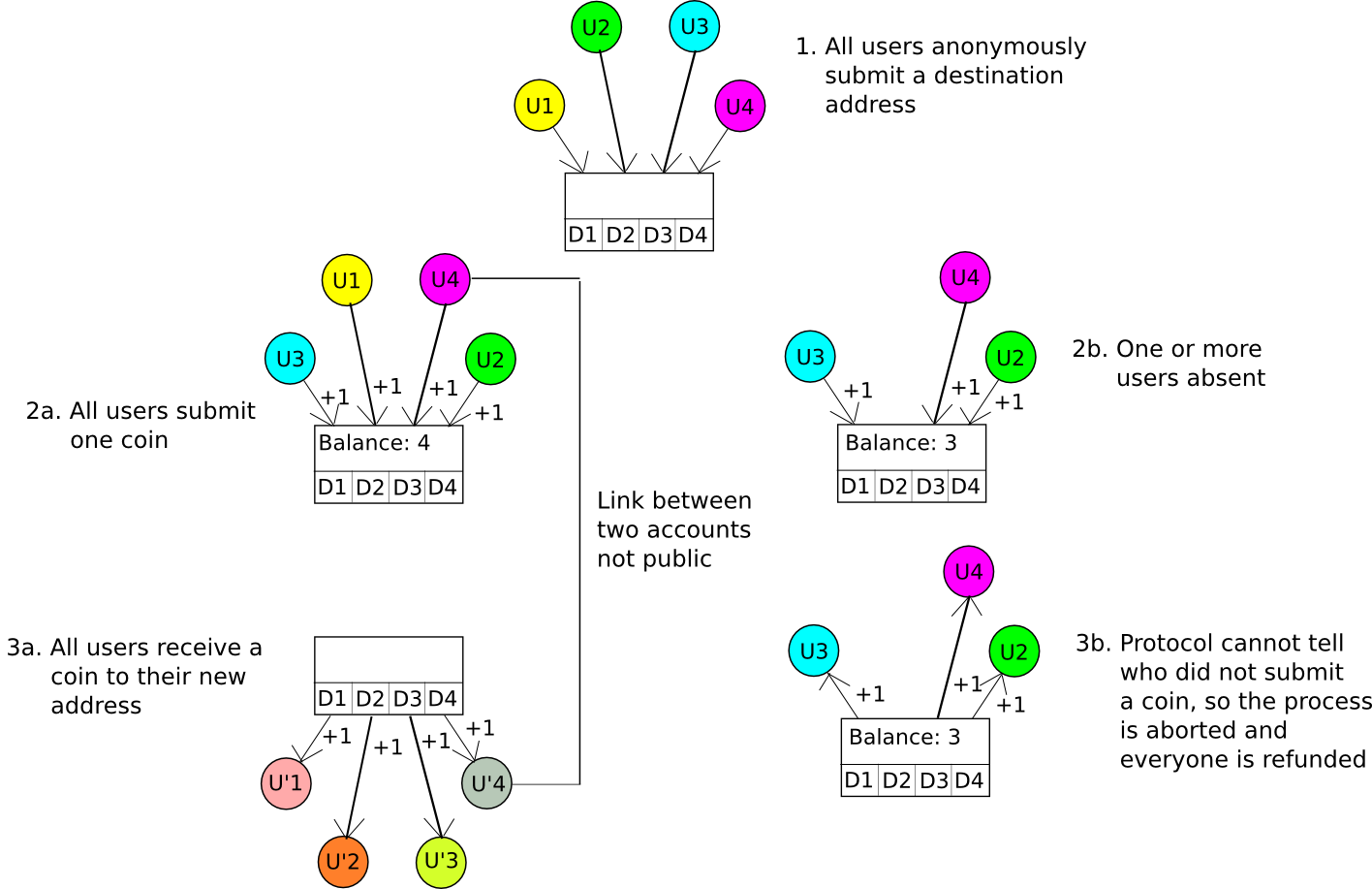
If all individuals are trustworthy and supply one coin, then everybody will put one coin in and get one coin out, however nobody will know which enter maps to which output. If at the very least one participant doesn’t put one coin in, then the method will fail, the cash will get refunded, and the entire individuals can strive once more. An algorithm much like this was applied by Amir Taaki and Pablo Martin for Bitcoin, and by Gavin Wood and Vlad Gluhovsky for Ethereum.
To this point, we’ve solely mentioned token anonymization. What about two-party sensible contracts? Right here, we use the identical mechanism as Hawk, besides we substitute the cryptography with easier cryptoeconomics – particularly, the “auditable computation” trick. The individuals ship their funds right into a contract which shops the hash of the code. When it comes time to ship out funds, both celebration can submit the outcome. The opposite celebration can both ship a transaction to agree on the outcome, permitting the funds to be despatched, or it could publish the precise code to the contract, at which level the code will run and distribute the funds accurately. A safety deposit can be utilized to incentivize the events to take part actually. Therefore, the system is personal by default, and provided that there’s a dispute does any info get leaked to the surface world.
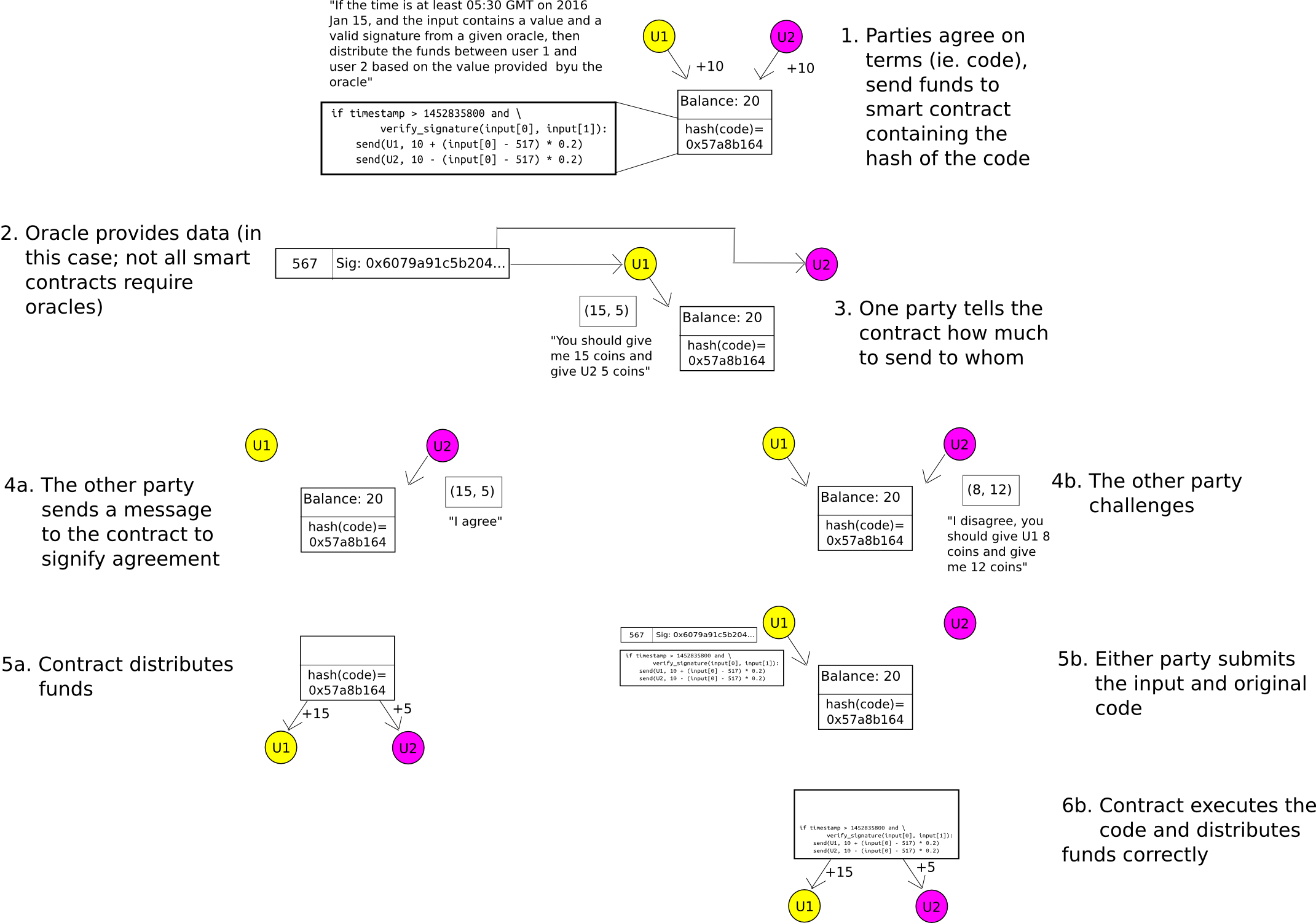
A generalization of this system known as state channels, and in addition has scalability advantages alongside its enhancements in privateness.
Ring Signatures
A know-how which is reasonably technically sophisticated, however extraordinarily promising for each token anonymization and id functions, is ring signatures. A hoop signature is actually a signature that proves that the signer has a personal key similar to one among a particular set of public keys, with out revealing which one. The 2-sentence clarification for the way this works mathematically is {that a} ring signature algorithm features a mathematical perform which could be computed usually with only a public key, however the place figuring out the personal key means that you can add a seed to the enter to make the output be no matter particular worth you need. The signature itself consists of an inventory of values, the place every worth is about to the perform utilized to the earlier worth (plus some seed); producing a sound signature requires utilizing information of a personal key to “shut the loop”, forcing the final worth that you simply compute to equal the primary. Given a sound “ring” produced on this method, anybody can confirm that it’s certainly a “ring”, so every worth is the same as the perform computed on the earlier worth plus the given seed, however there is no such thing as a approach to inform at which “hyperlink” within the ring a personal key was used.
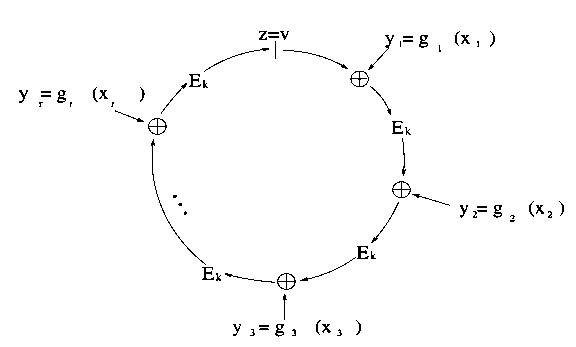
There’s additionally an upgraded model of a hoop signature referred to as a linkable ring signature, which provides an additional property: should you signal twice with the identical personal key, that truth could be detected – however no different info is revealed. Within the case of token anonymization, the applying is pretty easy: when a consumer desires to spend a coin, as an alternative of getting them present a daily signature to show possession of their public key straight, we mix public keys collectively into teams, and ask the consumer to easily show membership within the group. Due to the linkability property, a consumer that has one public key in a gaggle can solely spend from that group as soon as; conflicting signatures are rejected.
Ring signatures will also be used for voting functions: as an alternative of utilizing ring signatures to validate spending from a set of cash, we use them to validate votes. They will also be used for id functions: if you wish to show that you simply belong to a set of approved customers, with out revealing which one, ring signatures are well-suited for simply that. Ring signatures are extra mathematically concerned than easy signatures, however they’re fairly sensible to implement; some pattern code for ring signatures on high of Ethereum can be found here.
Secret Sharing and Encryption
Generally, blockchain functions usually are not making an attempt to mediate the switch of digital property, or report id info, or course of sensible contracts, and are as an alternative getting used on extra data-centric functions: timestamping, high-value information storage, proof of existence (or proof of inexistence, as within the case of certificates revocations), and so forth. A typical chorus is the thought of utilizing blockchains to construct methods the place “customers are answerable for their very own information”.
In these circumstances, it’s as soon as once more essential to notice that blockchains do NOT remedy privateness points, and are an authenticity resolution solely. Therefore, placing medical information in plaintext onto a blockchain is a Very Dangerous Concept. Nonetheless, they are often mixed with different applied sciences that do provide privateness as a way to create a holistic resolution for a lot of industries that does accomplish the specified objectives, with blockchains being a vendor-neutral platform the place some information could be saved as a way to present authenticity ensures.
So what are these privacy-preserving applied sciences? Effectively, within the case of easy information storage (eg. medical information), we will simply use the best and oldest one among all: encryption! Paperwork which can be hashed on the blockchain can first be encrypted, so even when the info is saved on one thing like IPFS solely the consumer with their very own personal key can see the paperwork. If a consumer desires to grant another person the precise to view some particular information in decrypted type, however not all of them, one can use one thing like a deterministic wallet to derive a special key for every doc.
One other helpful know-how is secret sharing (described in additional element here), permitting a consumer to encrypt a bit of knowledge in such a method that M of a given N customers (eg. M = 5, N = 9) can cooperate to decrypt the info, however no fewer.
The Way forward for Privateness
There are two main challenges with privateness preserving protocols in blockchains. One of many challenges is statistical: to ensure that any privacy-preserving scheme to be computationally sensible, the scheme should solely alter a small a part of the blockchain state with each transaction. Nonetheless, even when the contents of the alteration are privateness, there’ll inevitably be some quantity of metadata that isn’t. Therefore, statistical analyses will at all times be capable of work out one thing; at least, they may be capable of fish for patterns of when transactions happen, and in lots of circumstances they may be capable of slender down identities and work out who interacts with whom.
The second problem is the developer expertise problem. Turing-complete blockchains work very nicely for builders as a result of they’re very pleasant to builders which can be fully clueless in regards to the underlying mechanics of decentralization: they create a decentralized “world pc” which seems to be similar to a centralized pc, in impact saying “look, builders, you’ll be able to code what you have been planning to code already, besides that this new layer on the backside will now make all the pieces magically decentralized for you”. After all, the abstraction is just not good: excessive transaction charges, excessive latency, gasoline and block reorganizations are one thing new for programmers to deal with, however the limitations usually are not that giant.
With privateness, as we see, there is no such thing as a such magic bullet. Whereas there are partial options for particular use circumstances, and sometimes these partial options provide a excessive diploma of flexibility, the abstractions that they current are fairly totally different from what builders are used to. It isn’t trivial to go from “10-line python script that has some code for subtracting X cash from the sender’s steadiness and including X cash to the recipient’s steadiness” to “extremely anonymized digital token utilizing linkable ring signatures”.
Tasks like Hawk are very welcome steps in the precise course: they provide the promise of changing an arbitrary N-party protocol right into a zero-knowledge-ified protocol that trusts solely the blockchain for authenticity, and one particular celebration for privateness: basically, combining one of the best of each worlds of a centralized and decentralized method. Can we go additional, and create a protocol that trusts zero events for privateness? That is nonetheless an energetic analysis course, and we’ll simply have to attend and see how far we will get.
